AD Account Locked Out
Why do I keep get locked out of Active Directory?
Typically, account lockouts occur when you enter in a bad username/password combination that Active Directory is not expecting or enter in the incorrect information X number of times within the given threshold used for Active Directory. However, there are other instances where you may have locked out. The most common situations encountered here are noted below for reference:
Changing the password as directed or as needed and not letting the background replication via Active Directory to complete
Using one’s credentials for a service account and not updating the same when one changes their password
Leaving their sessions logged in at the console or in a remote session and not logging them out in a timely fashion before, during or after a password change
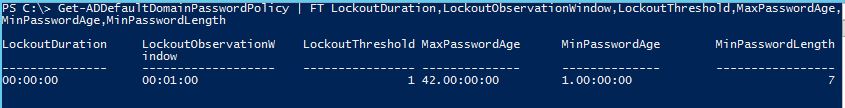
To Check the AD Account Policy, run the below Cmdlet in PowerShell
Get-ADDefaultDomainPasswordPolicy | FT LockoutDuration,LockoutObservationWindow,LockoutThreshold,MaxPasswordAge,MinPasswordAge,MinPasswordLength
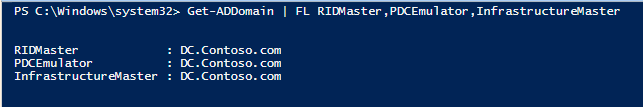
To Check the Locked-out Account details, Run the Below Cmdlets in PowerShell
#To Know your PDC emulator (Note: you can also use this to know your RID master and Infrastructure master)
Get-AdDomain | FL PDCEmulator,RIDMaster,InfrastructureMaster
#Two different log commands
Get-Command -Name Get-EventLog,Get-WinEvent
#To know syntax for Get-WinEvent
Get-Command -Name Get-WinEvent -Syntax
#Help for filterhashtable
Help Get-WinEvent -Parameter filterhashtable
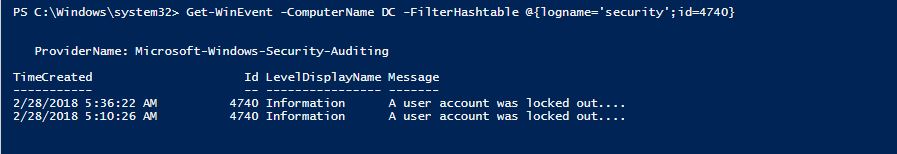
# Assuming DC as the PDC emulator here
Get-WinEvent -ComputerName DC -FilterHashtable @{logname='security';id=4740}
#4740 is the error code for account lockouts
#searching for logs from past 7 days
Get-WinEvent -ComputerName DC -FilterHashtable @{logname='security';id=4740;starttime=(Get-Date).AddDays(-7)}
If You want to know why the user account was locked. You can use the below Script to query on all the available DC’s
# Set up the lockout Report $Report = @() $User = "CN=Alaura Gate, OU=Contoso Users,OU=Contoso,DC=Contoso,DC=com" # Pick the DCs to crawl $DCs = Get-ADDomainController -Filter * | Select-Object HostName, IPv4Address, Site, OperatingSystem, OperationMasterRoles | Out-Gridview -Title "Select the DCs to query" -PassThru | Select-Object -ExpandProperty HostName # Find the lockout stats for that User on all selected DCs ForEach ($DC in $DCs) { $Report += Get-ADUser $User -Server $DC -ErrorAction Continue ` -Properties cn, LockedOut, pwdLastSet, badPwdCount, badPasswordTime, lastLogon, lastLogoff, lastLogonTimeStamp, whenCreated, whenChanged | ` Select-Object *, @{name='DC';expression={$DC}} } $DCs = $Report | Select-Object ` DC, ` cn, ` LockedOut, ` pwdLastSet, ` @{name='pwdLastSetConverted';expression={[datetime]::fromFileTime($_.pwdlastset)}}, ` badPwdCount, badPasswordTime, ` @{name='badPasswordTimeConverted';expression={[datetime]::fromFileTime($_.badPasswordTime)}}, ` lastLogon, ` @{name='lastLogonConverted';expression={[datetime]::fromFileTime($_.lastLogon)}}, ` lastLogoff, ` @{name='lastLogoffConverted';expression={[datetime]::fromFileTime($_.lastLogoff)}}, ` lastLogonTimeStamp, ` @{name='lastLogonTimestampConverted';expression={[datetime]::fromFileTime($_.lastLogonTimestamp)}}, ` whenCreated, ` whenChanged | Out-GridView -Title "Account Lockout Status from the Selected DC" -PassThru
Once you run the Script, it will give you a new window asking you to select the DC / DC’s to query. Select the DC you want as shown below and hit OK.
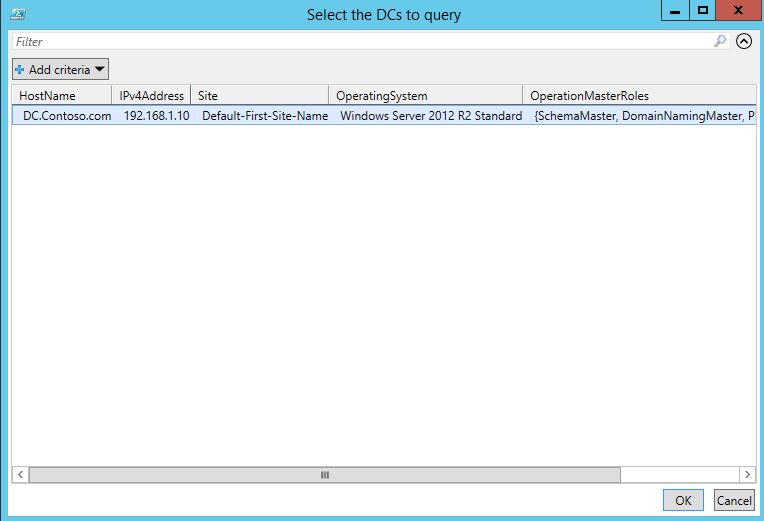
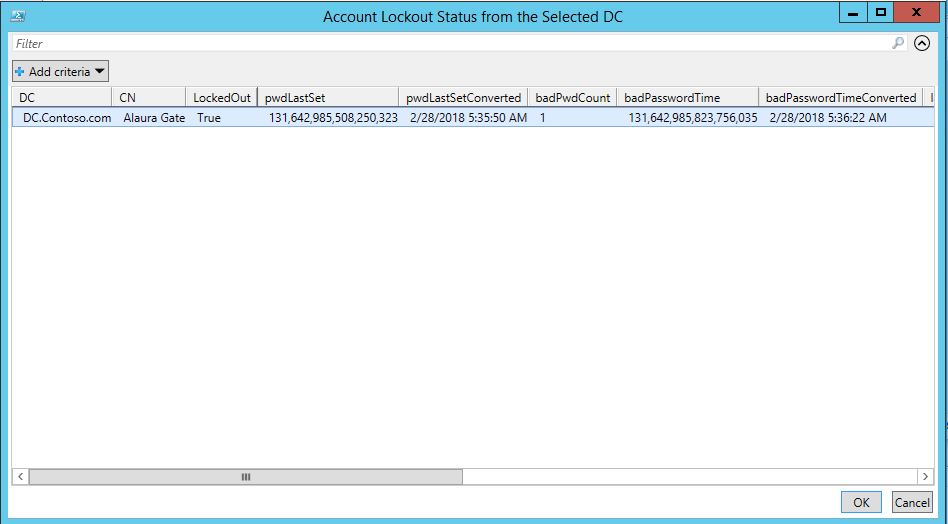
Once you hit OK, you will be prompted with a new window containing the user account details and Lockout Status, Bad password count and other few details which you may require.
![[How To]Use Event Logs in PowerShell Scripts img](https://www.theservergeeks.com/wp-content/uploads/2018/11/image-5.png)
![[How To] Create EventLog using PowerShell img](https://www.theservergeeks.com/wp-content/uploads/2018/11/image.png)